Category
Popular
-
 Acer Veriton X2670G (9 Liters)
₱29,380.00
Acer Veriton X2670G (9 Liters)
₱29,380.00
-
 i7 - XPS 8940
₱94,750.00
i7 - XPS 8940
₱94,750.00
-
 KASPERSKY - Comprehensive threat protection
KASPERSKY - Comprehensive threat protection
-
 GENIUS SLIMSTAR 130 USB KEYBOARD
₱530.00
GENIUS SLIMSTAR 130 USB KEYBOARD
₱530.00
-
 LEGION 5i 82AU00J8PH
₱63,740.00
LEGION 5i 82AU00J8PH
₱63,740.00
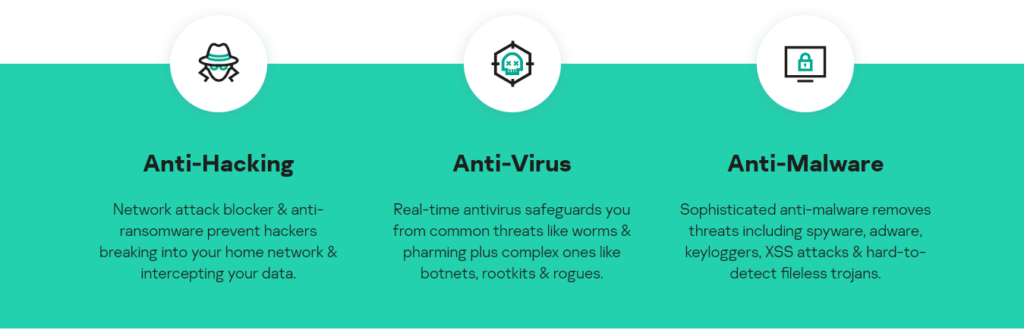
Our triple-layer security works 24/7 to guard your PC and data. It blocks common and complex threats like viruses, malware, spy apps, ransomware, plus defends your home network from hackers.
- Proactive detection
Searches out Windows vulnerabilities & threats - Real-time protection
Blocks cyberthreats before they take hold - Instant neutralization
Isolates & removes immediate dangers
Quick Comparison
| Settings | KASPERSKY - Comprehensive threat protection remove | IBM Db2 Database remove | ADOBE Enterprise remove | MICROSOFT OFFICE remove | TREND MICRO - Anti-malware and Advanced Threat Protection remove | SOPHOS Anti Malware Protection remove | ||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Name | KASPERSKY - Comprehensive threat protection remove | IBM Db2 Database remove | ADOBE Enterprise remove | MICROSOFT OFFICE remove | TREND MICRO - Anti-malware and Advanced Threat Protection remove | SOPHOS Anti Malware Protection remove | ||||||||||||||||||
| Image |  |  |  |  |  |  | ||||||||||||||||||
| SKU | ||||||||||||||||||||||||
| Rating | ||||||||||||||||||||||||
| Price | ||||||||||||||||||||||||
| Stock | ||||||||||||||||||||||||
| Availability | ||||||||||||||||||||||||
| Add to cart | ||||||||||||||||||||||||
| Description | Modernize your existing capabilities: All data, anywhere with IBM Db2 for IBM Cloud Pak for Data.What is IBM® Db2®?
IBM Db2 is a family of data management products, including the Db2 relational database. The products feature AI-powered capabilities to help you modernize the management of both structured and unstructured data across on premises and multicloud environments. By helping to make your data simple and accessible, the Db2 family positions your business to pursue the value of AI.
Now you can experience the enterprise readiness of Db2 products on an integrated data management and analytics platform, IBM Cloud Pak® for Data . Most of the Db2 family is available on the platform, either as an add-on or an included, data source service making virtually all of your data available across hybrid or multicloud environments to fuel your AI applications.
| Make experience your business.Digital has disrupted every industry. Your customers now expect you to be personal. To be beautiful. To be simple yet compelling. All the time. Businesses that can deliver on that will build loyalty that leads to growth. With Creative Cloud, Experience Cloud, and Document Cloud, we help you create amazing content, harness the power of your data, and accelerate your business processes. So you can design and deliver experiences that your customers will love. | Protect against the known, unknown, and undisclosed | Powerful, Enterprise-Grade AntivirusBlock and remove malware to defend against invasive threats.
Malware, ransomware, spyware, Trojans, phishing attacks. Whatever format they come in, we know one thing’s for sure: there’s a new virus created every few seconds and unleashed online. Organizations need enterprise-level antivirus protection that stays ahead of the next threat. Intercept X with EDR provides that.
| ||||||||||||||||||||
| Content |  Our triple-layer security works 24/7 to guard your PC and data. It blocks common and complex threats like viruses, malware, spy apps, ransomware, plus defends your home network from hackers.
Our triple-layer security works 24/7 to guard your PC and data. It blocks common and complex threats like viruses, malware, spy apps, ransomware, plus defends your home network from hackers.
| Deliver any data, anywhere
To support fast insights, you need a flexible data management foundation powered by modern technologies and agile enough to deliver data anywhere it’s needed.
IBM® Db2® Database on IBM Cloud Pak® for Data combines a proven, AI-infused, enterprise-ready data management system with an integrated data and AI platform built on the security-rich, scalable Red Hat® OpenShift® foundation. Derive insights with machine learning embedded into query processing. Cut costs with the multimodal capability that eliminates the need for data replication and migration. And enhance agility by running Db2 on any cloud vendor.
Modernize data managementDb2 for IBM Cloud Pak for Data enhances your data management with a containerized version of Db2, helping you expedite insights from proliferating data while managing costs and resources.
Accelerate data explorationData virtualization expands access to and visibility of all enterprise data.
Reduce operational costsContainerized deployments feature automated administration.
Enhance productivityContainerized microservices speed development life cycles.
Db2 Database benefits
IBM Db2 Database detailsIndustry-leading performance
Potential for 30% improvement in transactional response time⁶ with fast data retrieval and queries plus disk space compression
Advanced protection
Advanced authorization, encryption at rest and in transit, and comprehensive security controls for managing GDPR compliance
Continuous availability
Auto resynchronization and recovery plus clustering with IBM pureScale® to keep business running 24x7
Automated administration and tuning
Automatic setup, optimization, diagnostics and management of the database environment to save DBA time and cut maintenance costs
Multiple data types and languages
Flexible environment, integrates with multiple platforms plus supports NoSQL, pureXML, Graph and JSON; Java, .Net, Ruby, Python, Perl and more for building robust apps
Scaling
Elastic scaling up to 128 machines in multicloud and hybrid environments to reduce storage costs; data federation eliminates data silos
Database resource usageGet resource usage information for running or queued queries.
 Database throughputCheck the rate that data changes are retrieved, sent and applied on the target system.
 ScalabilityMonitor on-demand scalability in Db2 on Cloud to manage data needs.
 Data loadGet quick data transfer to Db2 on Cloud from cloud-based storage or your desktop.
 |
| MICROSOFT WINDOWS 10Do great things with WindowsAnyone can do anything with the right tools. Get tips, tricks and shortcuts to see how Windows 10 can help you. MICROSOFT OFFICE 365Build your future with Microsoft 365Get industry-leading apps combined with intelligent cloud services and world-class security. | 
The optimal blend of protection technique
Today’s sophisticated threats require a new approach to protecting users, networks, and data centers. This approach needs to use a blend of cross generational threat protection techniques that uses the right technique at the right time. Trend Micro XGen™ security provides that optimal blend of techniques.
Efficient, known threat detection.
Even though a threat is known, it doesn’t mean it’s less dangerous—it just means there is protection that already exists. This can come in the way of static analysis, signatures, or file and web databases. Known threat detection is considered the first phase of protection, and extremely critical. With a large number of attacks taking place on systems with unpatched software, known malware that is over 10 years old is still effectively being used today.
Detecting unknown threats.
Today, many advanced threats are designed specifically to bypass traditional security defenses and remain hidden while stealing your corporate data or encrypting devices for ransom. Non-signature based detection methods are designed to detect these kinds of attacks. These XGen™ security techniques include, but are not limited to, custom sandboxing, behavioral analysis, intrusion and exploit prevention, investigation and forensics, memory inspection, prevalence/maturity checks, and application control.
The importance of undisclosed vulnerabilities
The grey area between known and unknown is called undisclosed. These are software vulnerabilities that are only known by a small set of people (usually security researcher, security vendor, and impacted software vendor). Like an unknown hole in a fence, these vulnerabilities, if left unpatched, are potential targets for attacks. We offer ongoing threat prevention against emerging vulnerabilities through our Digital Vaccine service, often months before the vulnerability can be exploited by a threat.
| |||||||||||||||||||
| Weight | N/A | N/A | N/A | N/A | N/A | N/A | ||||||||||||||||||
| Dimensions | N/A | N/A | N/A | N/A | N/A | N/A | ||||||||||||||||||
| Additional information |
Related products
-
ORACLE DATABASE
Read moreOracle Database Technologies Oracle Database offers market-leading performance, scalability, reliability, and security, both on-premises and in the cloud. Oracle Database 19c is the current long term release, and it provides the highest level of release stability and longest time-frame for support and bug fixes. Oracle Database 21c, also available for production use today as an …
-
SOPHOS Anti Malware Protection
Read morePowerful, Enterprise-Grade Antivirus
Block and remove malware to defend against invasive threats.
Malware, ransomware, spyware, Trojans, phishing attacks. Whatever format they come in, we know one thing’s for sure: there’s a new virus created every few seconds and unleashed online. Organizations need enterprise-level antivirus protection that stays ahead of the next threat. Intercept X with EDR provides that.
-
ADOBE Enterprise
Read moreMake experience your business.
Digital has disrupted every industry. Your customers now expect you to be personal. To be beautiful. To be simple yet compelling. All the time. Businesses that can deliver on that will build loyalty that leads to growth. With Creative Cloud, Experience Cloud, and Document Cloud, we help you create amazing content, harness the power of your data, and accelerate your business processes. So you can design and deliver experiences that your customers will love.
Product Showcase




























Reviews
There are no reviews yet.